Form Authenticatoin – Claim Based Authentication :-
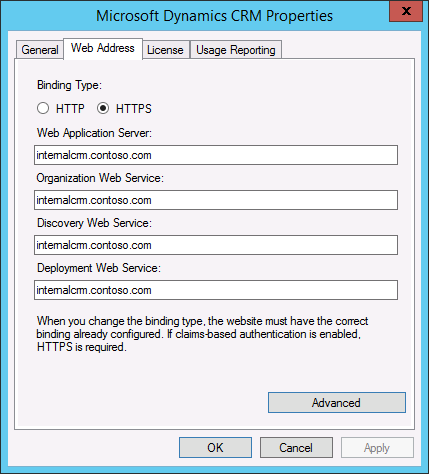
Set Microsoft Dynamics 365 Server binding to HTTPS and configure the root domain web addresses
Step 1: On the Microsoft Dynamics 365 server, start the Deployment Manager.
Step 2: In the Actions pane, click Properties.
Step 3: Click the Web Address tab.
Step 4: Under Binding Type, select HTTPS.
Step 5: Verify that the web addresses are valid for given TLS/SSL certificate and the TLS/SSL port bound to the Microsoft Dynamics 365 website.

Step 6: Click OK.
The CRMAppPool account and the Microsoft Dynamics CRM encryption certificate:
Step 1: On the Microsoft Dynamics 365 server, create a Microsoft Management Console (MMC) with the Certificates snap-in console that targets the Local computer certificate store.
Step 2: In the console tree, expand the Certificates (Local Computer) node, expand the Personal store, and then click Certificates.
Step 3: In the details pane, right-click the encryption certificate specified in the Configure Claims-Based Authentication Wizard, point to All Tasks, and then click Manage Private Keys.
Step 4: Click Add, add the CRMAppPool account, and then grant Read permissions.
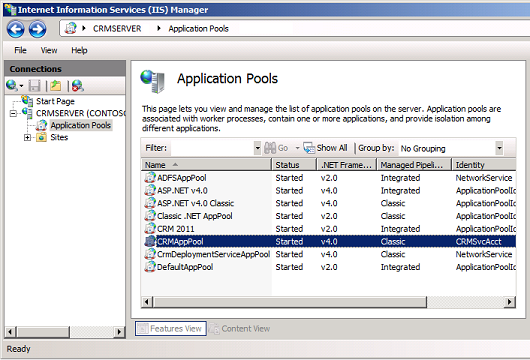
Step 5: Click OK.
Configuring claims-based authentication using the Configure Claims-Based Authentication Wizard:
Step 1: On the Microsoft Dynamics 365 server, start the Deployment Manager.
Step 2: In the Deployment Manager console tree, right-click Microsoft Dynamics 365, and then click Configure Claims-Based Authentication.
Step 3: Review the contents of the page, and then click Next.
Step 4: On the Specify the security token service page, enter the federation metadata URL.
Step 5: Click Next.
Step 6: On the Specify the encryption certificate page, specify the encryption certificate.
Step 7: Click Next.
Step 8: On the System Checks page, review the results, perform any steps required to fix problems, and then click Next.
Step 9: On the Review your selections verify your selections, and then click Apply.
Step 10: Click Finish.

